Leveraging an initial partnership with the TIMA Laboratory, we have the expertise to uniquely combine hardware security features and low-power in our solutions
Leveraging an initial partnership with the TIMA Laboratory, we have the expertise to uniquely combine hardware security features and low-power in our solutions
We provide development services for security primitives (TRNG, PUF, …) and cryptographic IPs (SHA3, etc.), as well as system integration, custom IP design, countermeasures, and attack simulations. Additionally, we offer expertise in physical implementation constraints related to security.
In order to meet your security objectives and propose the most appropriate solutions for your needs, we are also Common Criteria certified, an internationally recognized standard for evaluating the security of products and systems.
Discover our achievements in collaboration with SealSQ, developing quantum-resistant chip technology, and Tiempo Secure, with Common Criteria certification!

An STRNG is a TRNG (True Random Number Generator) based on a Self-Timed Ring Oscillator.
The objective of an STRNG is to generate truly random numbers from electronic noise in a proven, secure and efficient way.
Don’t waste time and energy waiting for the noise to accumulate, but rather capture it as quickly as possible by sampling a very jittery signal.
RTL design
Down to 10 pJ/bits
Up to 400 Mbits/s
In line with BSI's AIS 31 and NIST's SP 800-90B standards.
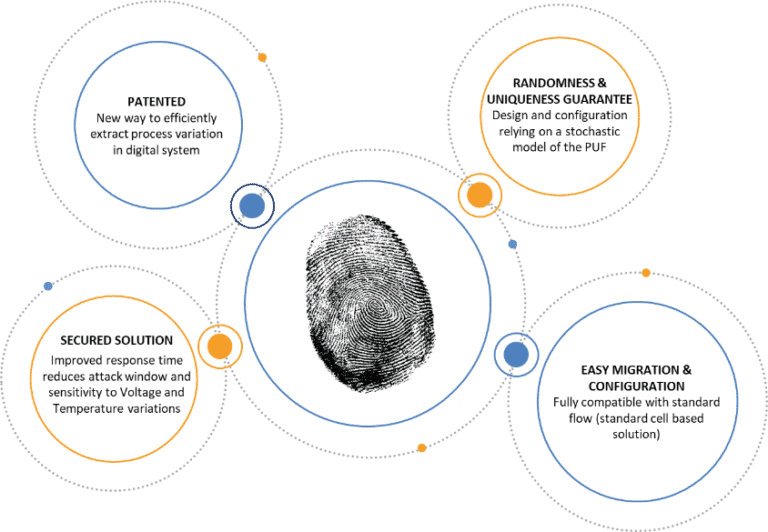
An STRPUF is a PUF (Physically Unclonable Function) based on a Self-Timed Ring Oscillator.
The objective is to extract the process variation to build a secret ID unique to the circuit.
An STRPUF enables device identification and/or authentication, software to hardware binding, or secure storage of cryptographic secrets.
Instead of capturing the delay variations through frequency measurements, directly extract the actual delay.
G. Gimenez, A. Cherkaoui and L. Fesquet, “A Self-Timed Ring based PUF,” 2020 26th IEEE International Symposium on Asynchronous Circuits and Systems (ASYNC), 2020

Our secure ASICs incorporate advanced post quantum cryptographic primitives, including SHA-3 hashing, ensuring optimal data protection against collision and preimage attacks.
The hardware implementation of SHA-3 offers increased energy efficiency and optimized performance for embedded and industrial applications.
Hardware-accelerated hashing for high performance.
Reduced power consumption compared to software implementations.
Enhanced security against quantum-based attacks.
Grégoire Gimenez, our physical implementation expert, presented practical information and best practices for designing random number generators (TRNGs).
A fantastic opportunity to explore innovation at the intersection of cybersecurity, AI, and integrated circuits (ASICs/ASSPs).


This event marks an important milestone in the new chapter following our integration with SEALSQ a great opportunity to strengthen our collaboration, align our visions, and build the future together!
This event feature industry experts to address the quantum computing revolution and post-quantum security solutions.
We work collaboratively with you to deliver a custom integrated circuit with competitive specifications and unique sensing capabilities.

Everything you need for a successful ASIC project from system concept to the delivery of packaged custom integrated chips.

Experienced with integrated electronics but need some support with your design?
The a-la-carte model is made for you.

Already developed your ASIC prototype?
We support you turning it into an industrial circuit and ramp up its production.